- MD4
-
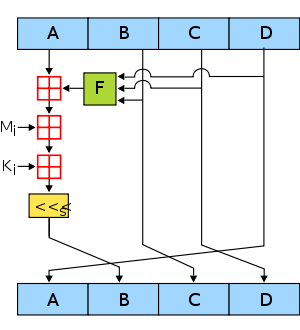
MD4 General Designers Ronald Rivest First published October 1990[1] Series MD2, MD4, MD5, MD6 Detail Digest sizes 128 bits Rounds 3 Best public cryptanalysis A collision attack published in 2007 can find collisions for full MD4 in less than 2 hash operations.[2] The MD4 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990.[3] The digest length is 128 bits. The algorithm has influenced later designs, such as the MD5, SHA-1 and RIPEMD algorithms.
The security of MD4 has been severely compromised. The first full collision attack against MD4 was published in 1995 and several newer attacks have been published since then. As of 2007, an attack can generate collisions in less than 2 MD4 hash operations.[2] A theoretical preimage attack also exists.
A variant of MD4 is used in the ed2k URI scheme to provide a unique identifier for a file in the popular eDonkey2000 / eMule P2P networks. MD4 is also used by the rsync protocol.
MD4 is used to compute NTLM password-derived key digests on Microsoft Windows NT, XP, Vista and 7.[4]
Contents
Security
Weaknesses in MD4 were demonstrated by Den Boer and Bosselaers in a paper published in 1991.[5] The first full-round MD4 collision attack was found by Hans Dobbertin in 1995, which took only seconds to carry out at that time.[6] In August 2004, Wang et al. found a very efficient collision attack, alongside attacks on later hash function designs in the MD4/MD5/SHA-1/RIPEMD family. This result was improved later by Sasaki et al., and generating a collision is now as cheap as verifying it (a few microseconds).[2]
In 2008, the preimage resistance of MD4 was also broken by Gaëtan Leurent, with a 2102 attack.[7] In 2011 RFC 6150 stated that RFC 1320 (MD4) is historic (obsolete).
MD4 hashes
The 128-bit (16-byte) MD4 hashes (also termed message digests) are typically represented as 32-digit hexadecimal numbers. The following demonstrates a 43-byte ASCII input and the corresponding MD4 hash:
MD4("The quick brown fox jumps over the lazy dog") = 1bee69a46ba811185c194762abaeae90
Even a small change in the message will (with overwhelming probability) result in a completely different hash, e.g. changing d to c:
MD4("The quick brown fox jumps over the lazy cog") = b86e130ce7028da59e672d56ad0113df
The hash of the zero-length string is:
MD4("") = 31d6cfe0d16ae931b73c59d7e0c089c0
MD4 Test Vectors
The following test vectors are defined in RFC 1320 (The MD4 Message-Digest Algorithm)
MD4 ("") = 31d6cfe0d16ae931b73c59d7e0c089c0 MD4 ("a") = bde52cb31de33e46245e05fbdbd6fb24 MD4 ("abc") = a448017aaf21d8525fc10ae87aa6729d MD4 ("message digest") = d9130a8164549fe818874806e1c7014b MD4 ("abcdefghijklmnopqrstuvwxyz") = d79e1c308aa5bbcdeea8ed63df412da9 MD4 ("ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789") = 043f8582f241db351ce627e153e7f0e4 MD4 ("12345678901234567890123456789012345678901234567890123456789012345678901234567890") = e33b4ddc9c38f2199c3e7b164fcc0536
See also
References
- Bert den Boer, Antoon Bosselaers: An Attack on the Last Two Rounds of MD4. Crypto 1991: 194–203
- Hans Dobbertin: Cryptanalysis of MD4. Fast Software Encryption 1996: 53–69
- Hans Dobbertin, 1998. Cryptanalysis of MD4. J. Cryptology 11(4): 253–271
- Xiaoyun Wang, Xuejia Lai, Dengguo Feng, Hui Chen, Xiuyuan Yu: Cryptanalysis of the Hash Functions MD4 and RIPEMD. Eurocrypt 2005: 1–18
- Yu Sasaki, Lei Wang, Kazuo Ohta, Noboru Kunihiro: New Message Difference for MD4. Fast Software Encryption 2007: 329–348
- ^ "The MD4 Message Digest Algorithm". Network Working Group. 1990-10. http://tools.ietf.org/html/rfc1186. Retrieved 2011-04-29.
- ^ a b c Yu Sasaki, et al. (2007). New message difference for MD4. http://www.iacr.org/archive/fse2007/45930331/45930331.pdf.
- ^ "What are MD2, MD4, and MD5?". Public-Key Cryptography Standards (PKCS): PKCS #7: Cryptographic Message Syntax Standard: 3.6 Other Cryptographic Techniques: 3.6.6 What are MD2, MD4, and MD5?. RSA Laboratories. http://www.rsa.com/rsalabs/node.asp?id=2253. Retrieved 2011-04-29.
- ^ "5.1 Security Considerations for Implementors". http://msdn.microsoft.com/en-us/library/cc236715(v=PROT.10).aspx. Retrieved 2011-07-21. "Deriving a key from a password is as specified in [RFC1320] and [FIPS46-2]."
- ^ Bert den Boer, Antoon Bosselaers (1991). An Attack on the Last Two Rounds of MD4. http://dsns.csie.nctu.edu.tw/research/crypto/HTML/PDF/C91/194.PDF.
- ^ Hans Dobbertin (1995-10-23). Cryptanalysis of MD4. http://www.springerlink.com/content/pkunhyvv7e5d9tbd/.
- ^ Gaëtan Leurent (2008-02-10). MD4 is Not One-Way. FSE 2008. http://www.di.ens.fr/~leurent/files/MD4_FSE08.pdf.
External links
- RFC 1320 - Description of MD4 by Ron Rivest
- RFC 6150 - MD4 to Historic Status
- On the Security of Encryption Modes of MD4, MD5 and HAVAL
- MD4 implementation in PHP and online
- Rivest, Ronald (1991). "The MD4 Message Digest Algorithm". Advances in Cryptology-CRYPT0’ 90 (Springer Berlin / Heidelberg). doi:10.1007/3-540-38424-3_22.
Collision Attacks
- An Attack on the Last Two Rounds of MD4
- Improved Collision Attack on MD4
- Fast MD4 Collision Generator (via Web Archive)
Cryptographic hash functions and message authentication codes (MACs) Common functions Functions SHA-3 finalists BLAKE · Grøstl · JH · Keccak · SkeinMAC algorithms Authenticated
encryption modesAttacks Misc. Standardization Cryptography Categories:- Cryptographic hash functions
- Broken hash functions
Wikimedia Foundation. 2010.