- Crypto-1
-
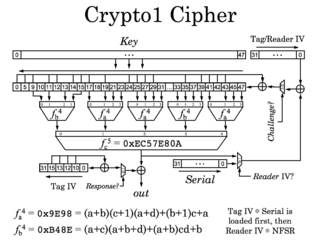
Crypto-1
NXP Crypto-1General Designers Philips/NXP First published October 6 2008 Cipher detail Key sizes 48 bits Security claims 48 bits Structure NLFSR, LFSR Best public cryptanalysis Garcia, Flavio D.; Peter van Rossum; Roel Verdult; Ronny Wichers Schreur (2009-03-17). "Wirelessly Pickpocketing a Mifare Classic Card" Crypto-1 is a proprietary encryption algorithm created by NXP Semiconductors specifically for Mifare RFID tags, including Oyster card, CharlieCard and OV-chipkaart.
Recent cryptographic research [1] [2] [3] [4] has shown that, "the security of this cipher is ... close to zero". Crypto-1 is a stream cipher very similar in its structure to its successor, Hitag2. Crypto-1 consists of
- one 48-bit feedback shift register for the main secret state of the cipher,
- a linear function,
- a two-layer 20-to-1 nonlinear function and
- a 16-bit LFSR which is used during the authentication phase (which also serves as the pseudo random number generator on some card implementations).
It can operate as an NLFSR and as an LFSR, depending on its input parameters. Outputs of one or both linear and nonlinear functions can be fed back into the cipher state or used as its output filters. The usual operation of Crypto-1 and Hitag2 ciphers uses nonlinear feedback only during the initialization/authentication stage, switching to operation as LFSR with a nonlinear output filter for encrypting the tag's communications in both directions.
External links
- Radboud Universiteit Nijmegen press release PDF (in English)
- NXP MF1 IC S50 data sheet PDF
- Details of Mifare reverse engineering by Henryk Plötz PDF (in German)
- C model of Crypto1 and code illustrating the hack
- Software-optimized Crypto-1 model
- Windows GUI Crypto1 tool, optimized for use with the Proxmark3
References
- ^ de Koning Gans, Gerhard; J.-H. Hoepman; F.D. Garcia (2008-03-15). "A Practical Attack on the MIFARE Classic". 8th Smart Card Research and Advanced Application Workshop (CARDIS 2008), LNCS, Springer. http://www.cs.ru.nl/~flaviog/publications/Attack.MIFARE.pdf.
- ^ Courtois, Nicolas T.; Karsten Nohl; Sean O'Neil (2008-04-14). "Algebraic Attacks on the Crypto-1 Stream Cipher in MiFare Classic and Oyster Cards". Cryptology ePrint Archive. http://eprint.iacr.org/2008/166.
- ^ Garcia, Flavio D.; Gerhard de Koning Gans; Ruben Muijrers; Peter van Rossum, Roel Verdult; Ronny Wichers Schreur; Bart Jacobs (2008-10-04). "Dismantling MIFARE Classic". 13th European Symposium on Research in Computer Security (ESORICS 2008), LNCS, Springer. http://www.cs.ru.nl/~flaviog/publications/Dismantling.Mifare.pdf.
- ^ Garcia, Flavio D.; Peter van Rossum; Roel Verdult; Ronny Wichers Schreur (2009-03-17). "Wirelessly Pickpocketing a Mifare Classic Card". 30th IEEE Symposium on Security and Privacy (S&P 2009), IEEE. http://www.cs.ru.nl/~flaviog/publications/Pickpocketing.Mifare.pdf.
Stream ciphers Theory: Shift register · LFSR · NLFSR · Shrinking generator · T-function · IV
Attacks: Correlation attack · Correlation immunity
Cryptography Categories:- Stream ciphers
- Cryptography stubs
Wikimedia Foundation. 2010.