- Root name server
-
 A Cisco 7301 router, part of the AMS-IX mirror of the K root-server.
A Cisco 7301 router, part of the AMS-IX mirror of the K root-server.
A root name server is a name server for the Domain Name System's root zone. It directly answers requests for records in the root zone and answers other requests returning a list of the designated authoritative name servers for the appropriate top-level domain (TLD). The root name servers are a critical part of the Internet because they are the first step in translating (resolving) human readable host names into IP addresses that are used in communication between Internet hosts.
A combination of limits in the DNS and certain protocols, namely the practical size of unfragmented User Datagram Protocol (UDP) packets, resulted in a limited number of root server addresses that can be accommodated in DNS name query responses. This limit has determined the number of name server installations at (currently) 13 clusters, serving the needs of the entire public Internet worldwide.
Contents
Root domain
The Domain Name System is a hierarchical naming system for computers, services, or any resource participating in the Internet. The top of that hierarchy is the root domain. The root domain does not have a formal name and its label in the DNS hierarchy is an empty string. All fully qualified domain names (FQDNs) on the Internet can be regarded as ending with this empty string for the root domain, and therefore ending in a full stop character (the label delimiter), e.g., www.example.com.. This is generally implied rather than explicit, as modern DNS software does not actually require that the terminating dot be included when attempting to translate a domain name to an IP address.
The root domain contains all top-level domains of the Internet. As of June 2009, there are 20 generic top-level domains (gTLDs) and 248 country code top-level domains (ccTLDs) in the root domain.[1] In addition, the ARPA domain is used for technical name spaces in the management of Internet addressing and other resources. A TEST domain is used for testing internationalized domain names.
Resolver operation
When a computer on the Internet needs to resolve a domain name, it uses resolver software to perform the lookup. A resolver breaks the name up into its labels from right to left. The first component (TLD) is requeried using a root server to obtain the responsible authoritative server. Queries for each label return more specific name servers until a name server returns the answer of the original query.
In practice, most of this information does not change very often over a period of hours and therefore it is cached by intermediate name servers or by a name cache built into the user's application. DNS lookups to the root nameservers may therefore be relatively infrequent. A survey in 2003 [2] reports that only 2% of all queries to the root servers were legitimate. Incorrect or non-existent caching was responsible for 75% of the queries, 12.5% were for unknown TLDs, 7% were for lookups using IP addresses as if they were domain names, etc. Some misconfigured desktop computers even tried to update the root server records for the TLDs. A similar list of observed problems and recommended fixes has been published in RFC 4697.
Although any local implementation of DNS can implement its own private root name servers, the term "root name server" is generally used to describe the thirteen well-known root name servers that implement the root name space domain for the Internet's official global implementation of the Domain Name System.
Root server addresses
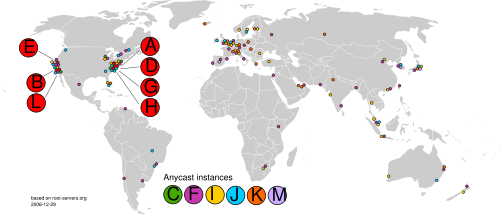
There are currently 13 root name servers specified, with names in the form letter.root-servers.net, where letter ranges from A to M. This does not mean there are 13 physical servers; each operator uses redundant computer equipment to provide reliable service even if failure of hardware or software occur. Additionally, nine of the servers operate in multiple geographical locations using a routing technique called anycast, providing increased performance and even more fault tolerance.
Ten servers were originally in the United States; some are now operated via anycast. Three servers were originally located in Stockholm (I), Amsterdam (K), and Tokyo (M).
Letter IPv4 address IPv6 address AS-number[3] Old name Operator Location
#sites (global/local)[4]Software A 198.41.0.4 2001:503:ba3e::2:30 AS19836 ns.internic.net Verisign Distributed using anycast
6/0BIND B 192.228.79.201 (since January 2004; originally was 128.9.0.107)[5] 2001:478:65::53 (not in root zone yet) none ns1.isi.edu USC-ISI Marina Del Rey, California, U.S.
0/1BIND C 192.33.4.12 2001:500:2::c (not in root zone yet) AS2149 c.psi.net Cogent Communications Distributed using anycast
6/0BIND D 128.8.10.90 2001:500:2d::d AS27 terp.umd.edu University of Maryland College Park, Maryland, U.S.
1/0BIND E 192.203.230.10 N/A AS297 ns.nasa.gov NASA Mountain View, California, U.S.
1/0BIND F 192.5.5.241 2001:500:2f::f AS3557 ns.isc.org Internet Systems Consortium Distributed using anycast
2/47BIND 9[6] G 192.112.36.4 N/A AS5927 ns.nic.ddn.mil Defense Information Systems Agency Distributed using anycast
6/0BIND H 128.63.2.53 2001:500:1::803f:235 AS13 aos.arl.army.mil U.S. Army Research Lab Aberdeen Proving Ground, Maryland, U.S.
2/0NSD I 192.36.148.17 2001:7fe::53 AS29216 nic.nordu.net Autonomica Distributed using anycast
36BIND J 192.58.128.30 (since November 2002; originally was 198.41.0.10) 2001:503:c27::2:30 AS26415 Verisign Distributed using anycast
63/7BIND K 193.0.14.129 2001:7fd::1 AS25152 RIPE NCC Distributed using anycast
5/13NSD[7] L 199.7.83.42 (since November 2007; originally was 198.32.64.12)[8] 2001:500:3::42 AS20144 ICANN Distributed using anycast
37/1NSD[9] M 202.12.27.33 2001:dc3::35 AS7500 WIDE Project distributed using anycast
5/1BIND Older servers had their own name before the policy of using similar names was established.
The choice of 13 nameservers was made because of limitations in the original DNS specification, which specifies a maximum packet size of 512 bytes when using the User Datagram Protocol (UDP).[10] The addition of IPv6 addresses for the root nameservers requires more than 512 bytes, which is facilitated by the EDNS0 extension to the DNS standard.[11] While only 13 names are used for the root nameservers, there are many more physical servers; A, C, F, I, J, K, L and M servers now exist in multiple locations on different continents, using anycast address announcements to provide decentralized service. As a result most of the physical root servers are now outside the United States, allowing for high performance worldwide.
There are also several alternative namespace systems with an alternative DNS root using their own set of root nameservers that exist in parallel to the mainstream nameservers. The first, AlterNIC, generated a substantial amount of press.[citation needed]
The function of a root name server may also be implemented locally, or on a provider network. Such servers are synchronized with the official root zone file as published by ICANN, and do not constitute an alternate root.
As the root nameservers are an important part of the Internet, they have come under attack several times, although none of the attacks have ever been serious enough to severely affect the performance of the Internet.
Root server supervision
The DNS Root Server System Advisory Committee is an ICANN committee. However, the root zone is controlled by the United States Department of Commerce who must approve all changes to the root zone file requested by ICANN. ICANN's bylaws[12] assign authority over the operation of the root nameservers of the Domain Name System to the DNS Root Server System Advisory Committee.
Root zone file
The root zone file is a small (about 200 kB) data set whose publication is the primary purpose of root nameservers.
The root zone file is at the apex of a hierarchical distributed database called the Domain Name System (DNS). This database is used by almost all Internet applications to translate worldwide unique names like www.wikipedia.org into other identifiers such as IP addresses.
The contents of the root zone file is a list of names and numeric IP addresses of the authoritative DNS servers for all top-level domains (TLDs) such as com, org, edu, or the country code top-level domains. On 12 December 2004, there were 258 TLDs and 773 different authoritative servers for those TLDs listed. Other name servers forward queries for which they do not have any information about authoritative servers to a root name server. The root name server, using its root zone file, answers with a referral to the authoritative servers for the appropriate TLD or with an indication that no such TLD exists.[13]
See also
- Distributed denial of service attacks on root nameservers
- EDNS0 (Extended DNS, version 0)
- Internet backbone
- Open Root Server Network
- Blackhole server
References
- ^ "List of top-level domains". ICANN. http://data.iana.org/TLD/tlds-alpha-by-domain.txt.
- ^ "Wow, That’s a Lot of Packets" (PDF). 2003. http://dns.measurement-factory.com/writings/wessels-pam2003-paper.pdf. Retrieved 2008-02-05.
- ^ AS-numbers and IP-adresses from Root-servers.org homepage checked 15 November 2010
- ^ Location and sites from Root-servers.org homepage checked 15 November 2010
- ^ "New IPv4 address for b.root-servers.net". http://www.root-servers.org/news/new-ip-b.html.
- ^ F-root | Internet Systems Consortium
- ^ K-root Homepage
- ^ "Advisory — “L Root” changing IP address on 1st November". ICANN. http://blog.icann.org/?p=227.
- ^ l.root-servers.net
- ^ RFC 1035 Domain names - implementation and specification
- ^ ICANN: Accommodating IP Version 6 Address Resource Records for the Root of the Domain Name System
- ^ ICANN Bylaws XI-2.3
- ^ ISOC, DNS Root Name Servers explained for the non-expert, (Available online, accessed 19 March 2010.)
- Notes
- Root Server Technical Operations Association
- Root Servers' Geographical Locations on Google Maps
- DNS Root Server System Advisory Committee
- DNS Root Name Servers Explained For Non-Experts
- DNS Root Name Servers Frequently Asked Questions
- Location of Root servers in Asia-Pacific
- Bogus Queries received at the Root Servers
- ORSN, Open Root Server Network with IPv6 support in europe
- RFC 2826 - IAB Technical Comment on the Unique DNS Root
- RFC 2870 - Root Name Server Operational Requirements
- RFC 4697 - Observed DNS Resolution Misbehavior (from observations on the Root Servers)
External links
Categories:
Wikimedia Foundation. 2010.