- Duqu
-
Duqu is a computer worm discovered on 1 September 2011, thought to be related to the Stuxnet worm. The Laboratory of Cryptography and System Security (CrySyS)[1] of the Budapest University of Technology and Economics in Hungary, which discovered the threat, analyzed the malware and wrote a 60-page report[2], naming the threat Duqu.[3] Duqu got its name from the prefix "~DQ" it gives to the names of files it creates.[4]
Contents
The Duqu term
The Duqu term identifies several different meanings:
- Duqu malware is a variety of software components that together provide services to the attackers. Currently this includes information stealing capabilities and in the background, kernel drivers and injection tools.
- Duqu flaw is the flaw in Microsoft Windows that is used in malicious files to execute malware components of Duqu. Currently one flaw is known, a TTF related problem in win32k.sys.
- Operation Duqu is the process of using Duqu for unknown goals. The operation might be related to Operation Stuxnet.
Relationship to Stuxnet
Symantec, based on the CrySyS report, continued the analysis of the threat, which it called "nearly identical to Stuxnet, but with a completely different purpose", and published a detailed technical paper on it with a cut-down version of the original lab report as an appendix.[5][4] Symantec believes that Duqu was created by the same authors as Stuxnet, or that the authors had access to the source code of Stuxnet. The worm, like Stuxnet, has a forged digital certificate, and collects information to prepare for future attacks.[4][6] Mikko Hyppönen, Chief Research Officer for F-Secure, said that Duqu's kernel driver, JMINET7.SYS, was so similar to Stuxnet's MRXCLS.SYS that F-Secure's back-end system thought it was Stuxnet. Hyppönen further said that Duqu's own digital certificate was stolen from C-Media, located in Taipei, Taiwan. The certificates were due to expire on 2 August 2012 but were revoked on 14 October 2011 according to Symantec.[5]
Another source, Dell SecureWorks, reports that Duqu may not be related to Stuxnet.[7]
Microsoft Word zero-day exploit
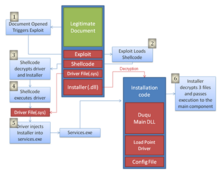
Like Stuxnet, Duqu attacks Windows systems using a zero-day vulnerability. The first-known installer (AKA dropper) file recovered and disclosed by CrySyS Lab uses a Microsoft Word (.doc) that exploits the Win32k TrueType font parsing engine and allows execution.[8] Duqu dropper relates to font embedding, and thus relates to the workaround to restrict access to T2EMBED.DLL, which is a TrueType font parsing engine.[9] "Microsoft is collaborating with our partners to provide protections for a vulnerability used in targeted attempts to infect computers with the Duqu malware. We are working diligently to address this issue and will release a security update for customers through our security bulletin process", Jerry Bryant, group manager of response communications in Microsoft's Trustworthy Computing group said in a statement on 3 November 2011.[10] However, Microsoft did not include a patch for the vulnerability in the batch of patches issued on 8 November 2011.[11]
Purpose
Duqu uses the peer-to-peer SMB protocol to move in secure networks from less secure areas to the secure zone.[4] According to McAfee, one of Duqu's actions is to steal digital certificates from attacked computers to help future viruses appear as secure software.[12] Duqu uses a 54×54 pixel jpeg file (364.5 bytes) and encrypted dummy files as containers to smuggle data to its command and control center. Security experts are still analyzing code to determine what information the communications contain. Initial research indicates that the virus automatically removes itself after 36 days, which would limit its detection.[5]
Key points are:
- Executables developed after Stuxnet using the Stuxnet source code have been discovered.
- The executables are designed to capture information such as keystrokes and system information.
- Current analysis shows no code related to industrial control systems, exploits, or self-replication.
- The executables have been found in a limited number of organizations, including those involved in the manufacturing of industrial control systems.
- The exfiltrated data may be used to enable a future Stuxnet-like attack.
Additional Resources
Additional up-to-date references include technical reports, blog posts, articles, tools, etc. are also available on the SCADAhacker website at this link. This website is maintained by a group of professionals focused on cyber security as it relates to industrial control systems (aka SCADA) and how they are used to command and control critical infrastructure.
See also
- Stars virus
- Cyber electronic warfare
- Cyber security standards
- Cyberwarfare in the United States
- List of cyber attack threat trends
- Operation Merlin
- Proactive Cyber Defence
- United States Cyber Command
- Moonlight Maze
- Titan Rain
References
- ^ "Laboratory of Cryptography and System Security (CrySyS)". http://www.crysys.hu/. Retrieved 4 November 2011.
- ^ "Duqu: A Stuxnet-like malware found in the wild, technical report". Laboratory of Cryptography of Systems Security (CrySyS). 14 October 2011. http://www.crysys.hu/publications/files/bencsathPBF11duqu.pdf.
- ^ "Statement on Duqu's initial analysis". Laboratory of Cryptography of Systems Security (CrySyS). 21 October 2011. http://www.crysys.hu/in-the-press.html. Retrieved 25 October 2011.
- ^ a b c d "W32.Duqu – The precursor to the next Stuxnet (Version 1.2)". Symantec. 20 October 2011. http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w32_duqu_the_precursor_to_the_next_stuxnet.pdf. Retrieved 25 October 2011.
- ^ a b c Zetter, Kim (18 October 2011). "Son of Stuxnet Found in the Wild on Systems in Europe". http://www.wired.com/threatlevel/2011/10/son-of-stuxnet-in-the-wild/. Retrieved 21 October 2011.
- ^ "Virus Duqu alarmiert IT-Sicherheitsexperten". Die Zeit. 19 October 2011. http://www.zeit.de/digital/internet/2011-10/computerwurm-duqu-stuxnet. Retrieved 19 October 2011.
- ^ "Spotted in Iran, trojan Duqu may not be "son of Stuxnet" after all". http://arstechnica.com/business/news/2011/10/spotted-in-iran-trojan-duqu-may-not-be-son-of-stuxnet-after-all.ars?utm_source=rss&utm_medium=rss&utm_campaign=rss. Retrieved 27 October 2011.
- ^ "Microsoft issues temporary 'fix-it' for Duqu zero-day". http://www.zdnet.com/blog/security/microsoft-issues-temporary-fix-it-for-duqu-zero-day/9764. Retrieved 5 November 2011.
- ^ "Microsoft Security Advisory (2639658)". Vulnerability in TrueType Font Parsing Could Allow Elevation of Privilege. 3 November 2011.
- ^ "Stuxnet-like virus hides in Microsoft Word files". ABS-CBN News. 4 November 2011. http://www.abs-cbnnews.com/lifestyle/11/04/11/stuxnet-virus-hides-microsoft-word-files. Retrieved 9 November 2011.
- ^ Tony Bradley (8 November 2011). "Microsoft Leaves Duqu Worm Exploit Unpatched". PCWorld.
- ^ Venere, Guilherme; Szor, Peter (18 October 2011). "The Day of the Golden Jackal – The Next Tale in the Stuxnet Files: Duqu". McAfee. http://blogs.mcafee.com/mcafee-labs/the-day-of-the-golden-jackal-%E2%80%93-further-tales-of-the-stuxnet-files. Retrieved 19 October 2011.
Categories:- Exploit-based worms
- Cyberwarfare
Wikimedia Foundation. 2010.