- Content Scramble System
-
Content Scramble System (CSS)
CSS in CGeneral Designers DVD Forum First published 1996 Cipher detail Key sizes 40 bits Security claims 240 Block sizes 2048 bytes (DVD sector size) Structure Stream cipher Best public cryptanalysis Defeated in 1999 by DeCSS, 40-bit key size is subject to brute-force attack, effective key size is about 16 bits. This can be brute-forced in about a minute by a Pentium II. Content Scramble System (CSS) is a Digital Rights Management (DRM) and encryption system employed on almost all commercially produced DVD-Video discs. CSS utilizes a proprietary 40-bit stream cipher algorithm. The system was introduced around 1996 and was first compromised in 1999.
The purpose of CSS is twofold:
- CSS prevents byte-for-byte copies of an MPEG (digital video) stream from being playable since such copies do not include the keys that are hidden on the lead-in area of the restricted DVD.
- CSS provides a reason for manufacturers to make their devices compliant with an industry-controlled standard, since CSS scrambled discs cannot in principle be played on noncompliant devices; anyone wishing to build compliant devices must obtain a license, which contains the requirement that the rest of the DRM system (region codes, Macrovision, and user operation prohibition) be implemented.[1]
While most CSS-decrypting software is used to play DVD videos, other pieces of software (such as DVD Decrypter, AnyDVD, DVD43, Smartripper, and DVD Shrink) can copy a DVD to a hard drive and remove Macrovision, CSS encryption, region codes, and User operation prohibition.
CSS has been superseded by newer DRM schemes such as Content Protection for Recordable Media (CPRM), or by Advanced Encryption Standard (AES) in the Advanced Access Content System (AACS) DRM scheme used by HD DVD and Blu-ray Disc, which have 56-bit and 128-bit key sizes, respectively, providing a much higher level of security than the 40-bit key size of CSS.
Contents
Terminology
- Authentication
- a process for a DVD drive and CSS Decryption module to recognize (or authenticate) each other; this is normally necessary before reading data from a CSS-encrypted DVD, and an authentication key is used for this purpose. Authentication can be bypassed with a brute-force attack (see below).
- Title key
- used for scrambling and descrambling DVD data known collectively as a title, which could be a complete motion picture, a trailer, or some similar self-contained unit.
- Disc key
- used for decrypting a title key on a DVD.
- Player key
- used for decrypting a disc key on a DVD; each DVD player manufacturer is allocated one of approximately 400 player keys to incorporate in its players.
Method
The generic term CSS key may refer to an authentication key used in the CSS secure handshake with a descrambler, a disc key, a player key, a title key, a secured disk key set, or an encrypted title key.
The CSS key sets are licensed by the DVD Copy Control Association to manufacturers who incorporate them into products such as DVD movie releases, drives, and players; most DVD players are equipped with a CSS Decryption module.
Disc keys are stored on the lead-in area of the disc, an area that a compliant drive is only supposed to read in a special way; the sectors of the DVD are encrypted, preventing the copying of VOB (Video Object) content, which can only be retrieved with authentication keys.[2] Furthermore, the key area on a DVD-R disc is immutable, thus preventing the trivial copying of a CSS-encrypted DVD to a DVD-R. However, the key area on a DVD+R disc is mutable, but standard drives have refused to write to it (with the exception of the Book type field, which is used for bitsetting). Keys can be passed from a DVD drive to a descrambler over a data bus using a secure (but now compromised) handshake protocol.[1]
Cryptanalysis
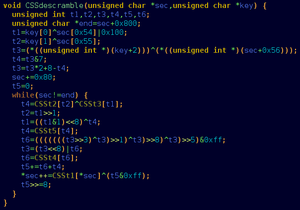
In October 1999, Jon Lech Johansen and two people who have remained anonymous reverse engineered CSS and created DeCSS to share the exploit with others, in a striking example of the trusted client problem. Not long after, CSS was further revealed to be easily susceptible to a brute force attack, which is implemented by the widely used libdvdcss; the brute-force attack works even if the keys cannot be retrieved from the lead-in area, as is the case when the DVD's region code is different from that of the drive. This allows region-free DVD player software to work with region-locked drives.
CSS's weakness is primarily due to the regulations placed on the export of cryptographic systems from the United States;[3] at the time that CSS was introduced, it was forbidden to export systems that employ keys in excess of 40 bits, a key length that had already been proven to be wholly inadequate in the face of increasing computer processing power (see Data Encryption Standard). In addition, structural flaws in CSS reduce the effective key length to only around 16 bits, allowing for CSS to be compromised in less than a minute by brute-force with a 450 MHz processor;[4]. A 450 MHz processor is the official minimum computational requirement[citation needed] for playing an unencrypted DVD-compliant MPEG-2 videostream, so this effectively means that any computer that can decode a DVD entirely in software can also crack a CSS-encrypted DVD.
In Geeks Bearing Gifts, author Ted Nelson states "DVD encryption was intentionally made light by the DVD encryption committee, based on arguments in a libertarian book Computer Lib.", a claim cited as originating from personal communication with an anonymous source; Nelson also wrote Computer Lib.[5]
See also
- Disc wobble
- DVD Copy Control Association
- Advanced Access Content System
- AnyDVD, DVD43, DeCSS, DVD Decrypter, Smartripper
- Content Protection for Prerecorded Media (CPPM)
- Fair use
- ARccOS: an additional form of DVD copy protection
- libdvdcss, a free software, region-free library for accessing CSS-encypted DVDs, thus enabling playback of such discs on opensource players.
References
- ^ a b IEEE - Copy Protection for DVD Video p.2
- ^ CSS - A butt of all the jokes
- ^ Export of cryptography in the United States
- ^ Frank A. Stevenson (1999-11-08). Cryptanalysis of Contents Scrambling System. http://web.archive.org/web/20000302000206/www.dvd-copy.com/news/cryptanalysis_of_contents_scrambling_system.htm. Archive.org
- ^ Nelson, Ted (2008). Geeks bearing gifts : how the computer world got this way (Ed. 1.0. ed.). Sausalito, CA: Mindful Press. pp. 199. ISBN 978-0-578-00438-9.
External links
Categories:- Block ciphers
- History of cryptography
- Digital rights management
- Optical disc copy protection
- Broken stream ciphers
- DVD
- History of television
Wikimedia Foundation. 2010.