- Alice and Bob
-
The names Alice and Bob are commonly used placeholder names for archetypal characters in fields such as cryptography and physics. The names are used for convenience; for example, "Alice sends a message to Bob encrypted with his public key" is easier to follow than "Party A sends a message to Party B encrypted by Party B's public key." Following the alphabet, the specific names have evolved into common parlance within these fields—helping technical topics to be explained in a more understandable fashion.
In cryptography and computer security, there are a number of widely used names for the participants in discussions and presentations about various protocols. The names are conventional, somewhat self-suggestive, sometimes humorous, and effectively act as metasyntactic variables.
In typical implementations of these protocols, it is understood that the actions attributed to characters such as Alice or Bob need not always be carried out by human parties directly, but also by a trusted automated agent (such as a computer program) on their behalf. Despite the advantage of Alice and Bob's distinct genders in reducing ambiguity, there has been little tendency to introduce inanimate parties so they could be referred by neuter pronouns.
Contents
List of characters
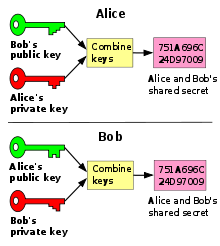
 Alice and Bob diagram used to explain public-key cryptography.
Alice and Bob diagram used to explain public-key cryptography.
This list is drawn mostly from the book Applied Cryptography by Bruce Schneier. Alice and Bob are archetypes in cryptography; Eve is also common. Names further down the alphabet are less common.
- Alice and Bob. Generally, Alice wants to send a message to Bob. These names were used by Ron Rivest in the 1978 Communications of the ACM article presenting the RSA cryptosystem, and in A Method for Obtaining Digital Signatures and Public-Key Cryptosystems published April 4, 1977, revised September 1, 1977 as technical Memo LCS/TM82. Rivest denies that these names have any relation to the 1969 movie Bob & Carol & Ted & Alice as occasionally suggested by others.[citation needed]
- Carol, Carlos or Charlie, as a third participant in communications.
- Chuck, as a third participant usually of malicious intent.[1]
- Dave, a fourth participant, and so on alphabetically.
- Eve, an eavesdropper, is usually a passive attacker. While she can listen in on messages between Alice and Bob, she cannot modify them. In quantum cryptography, Eve may also represent the environment.
- Mallory, a malicious attacker (less commonly called Trudy, an intruder.); unlike Eve, Mallory can modify messages, substitute her own messages, replay old messages, and so on. The difficulty of securing a system against Mallory is much greater than against Eve.
- Peggy, a prover, and Victor, a verifier, often must interact in some way to show that the intended transaction has actually taken place. They are often found in zero-knowledge proofs.
- Trent, a trusted arbitrator, is some kind of neutral third party, whose exact role varies with the protocol under discussion.
- Walter, a warden, may be needed to guard Alice and Bob in some respect, depending on the protocol being discussed.
Although an interactive proof system is not quite a cryptographic protocol, it is sufficiently related to mention the cast of characters its literature features:
- Arthur and Merlin: In interactive proof systems, the prover has unbounded computational ability and is hence associated with Merlin, the powerful wizard. He claims the truth of a statement, and Arthur, the wise king, questions him to verify the claim. These two characters also give the name for two complexity classes, namely MA and AM.
A similar pair of characters is Paul and Carole. The characters were introduced in the solution of the Twenty Questions problem,[2] where "Paul", who asked questions, stood for Paul Erdős and "Carole", who answered them, was an anagram of "oracle". They were further used in certain combinatorial games in the roles of Pusher and Chooser respectively, and have since been used in various roles.[3]
See also
- Dave and Sue
- John Doe
- George Spelvin
- Metasyntactic variable
- Ruritania, a fictional country sometimes used like personal names Alice and Bob as a generic country
- Tommy Atkins
Notes
- ^ Tanenbaum, Andrew S. (2007), Distributed Systems: Principles and Paradigms, Pearson Prentice Hall, p. 171;399–402, ISBN 978-0-13-239227-3, http://books.google.com/?id=DL8ZAQAAIAAJ
- ^ Spencer, Joel; Winkler, Peter (1992), "Three Thresholds for a Liar", Combinatorics, Probability and Computing 1 (01): 81–93, doi:10.1017/S0963548300000080, http://math.dartmouth.edu/~pw/papers/3thresh.ps
- ^ Muthukrishnan, S. (2005), Data Streams: Algorithms and Applications, Now Publishers, p. 3, ISBN 978-1-933019-14-7, http://algo.research.googlepages.com/eight.ps
References
- C.H. Lindsey, Regulation of Investigatory Powers Bill: Some Scenarios, 2000, [1].
External links
- A Method for Obtaining Digital Signatures and Public-Key Cryptosystems
- John Gordon (April 1984). "Extract from the Alice and Bob After-Dinner Speech". http://www.johngordonsweb.co.uk/concept/alicebob.html. Retrieved 2010-03-30.
- Geek Song: "Alice and Bob"
- Alice and Bob jokes (mainly Quantum Computing-related)
- Alice and Bob: IT's inseparable couple
- A short history of Bobs (story and slideshow) in the computing industry, from Alice & Bob to Microsoft Bob and Father of Ethernet Bob Metcalfe
- Alice and Bob Recopilatory
Categories:- Cryptographic protocols
- Placeholder names
Wikimedia Foundation. 2010.