- Mix network
-
This article is about cryptographic concept. For the social network, see The Mix Network.
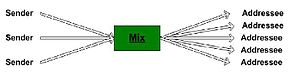
Digital mixes (also known as mix networks) were invented by David Chaum in 1981. Digital mixes create hard-to-trace communications by using a chain of proxy servers. Each message is encrypted to each proxy using public key cryptography; the resulting encryption is layered like a Russian doll (except that each "doll" is of the same size) with the message as the innermost layer. Each proxy server strips off its own layer of encryption to reveal where to send the message next. If all but one of the proxy servers are compromised by the tracer, untraceability can still be achieved against some weaker adversaries.
Some anonymous remailers (such as Mixmaster) and onion routing (including Tor) are based on this idea.
There is another kind of mix net that consists of re-encryption operations. In these mixnets each mix node re-encrypts the set of received messages and the decryption is done in a single step. Homomorphic encryption schemes allow that.
Contents
How it works
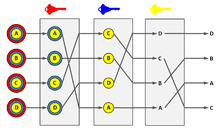
Participant A prepares a message for delivery to participant B by appending a random value to the message, sealing it with the addressee's public key Kb, appending B’s address, and then sealing the result with the mix's public key Km. M opens it with his private key, now he knows B’s address, and he sends Kb(message,R) to B.
Message format

To accomplish this, the sender takes the mix’s public key (Km), and uses it to encrypt an envelope containing a random string (R1), a nested envelope addressed to the recipient, and the email address of the recipient (B). This nested envelope is encrypted with the recipient’s public key (Kb), and contains another random string (R0), along with the body of the message being sent. Upon receipt of the encrypted top-level envelope, the mix uses its secret key to open it. Inside, it finds the address of the recipient (B) and an encrypted message bound for B. The random string (R1) is discarded.
Return Addresses
What is needed now is a way for B to respond to A while still keeping the identity of A secret from B.
A solution is for A to form an untraceable return address K1(S1,Ax),Kx where Ax is its own real address, Kx is a public one-time key chosen for the current occasion only, and S1 is a key that will also act as a random string for purposes of sealing. Then, A can send this return address to B as part of a message sent by the techniques already described.
B sends K1(S1,A),Kx(S0,response) to M, and M transforms it to A,S1(Kx(S0,response).
This mix uses the string of bits S1 that it finds after decrypting the address part K1(S1,A) as a key to re-encrypt the message part Kx(S0,response). Only the addressee, A, can decrypt the resulting output because A created both S1 and Kx. The additional key Kx assures that the mix cannot see the content of the reply-message.
The following indicates how B uses this untraceable return address to form a response to A, via a new kind of mix:
The message from A
 B:
B:
Reply message from B
 A:
A:
Where: Kb = B’s public key, K1 = the mix’s public key.
A destination can reply to a source without sacrificing source anonymity. The reply message shares all of the performance and security benefits with the anonymous messages from source to destination.
Goals
The purpose of a mix is to hide the correspondences between the items in its input and those in its output. (Note: if just one item is repeated in the input and allowed to be repeated in the output, then the correspondence is revealed for that item). By routing through numerous mixes in the network, determining who is talking to who is made even more difficult.
Further reading
- Email Security, Bruce Schneier (ISBN 0-471-05318-X)
- Computer Privacy Handbook, Andre Bacard (ISBN 1-56609-171-3)
References
Categories:
Wikimedia Foundation. 2010.