- Zombie (computer science)
-
This article is about the computing term. For the Irish electro band, see Zombie Computer (Band)."Zombie virus" redirects here. For the use of the term in science fiction, see Zombie apocalypse.
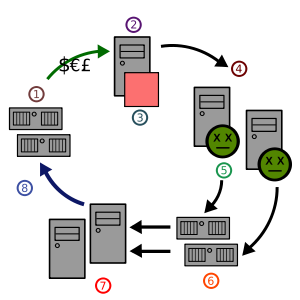
In computer science, a zombie is a computer connected to the Internet that has been compromised by a cracker, computer virus or trojan horse and can be used to perform malicious tasks of one sort or another under remote direction. Botnets of zombie computers are often used to spread e-mail spam and launch denial-of-service attacks. Most owners of zombie computers are unaware that their system is being used in this way. Because the owner tends to be unaware, these computers are metaphorically compared to zombies.
History
Zombies have been used extensively to send e-mail spam; as of 2005, an estimated 50–80% of all spam worldwide was sent by zombie computers.[1] This allows spammers to avoid detection and presumably reduces their bandwidth costs, since the owners of zombies pay for their own bandwidth. This spam also greatly furthers the spread of Trojan horses; as Trojans, they are not self-replicating. They rely on the movement of e-mails or spam to grow, whereas worms can spread by other means.[2]
For similar reasons zombies are also used to commit click fraud against sites displaying pay per click advertising. Others can host phishing or money mule recruiting websites.
Zombies can be used to conduct distributed denial-of-service attacks, a term which refers to the orchestrated flooding of target websites by large numbers of computers at once. The large number of Internet users making simultaneous requests of a website's server are intended to result in crashing and the prevention of legitimate users from accessing the site.[3] A variant of this type of flooding is known as distributed degradation-of-service. Committed by "pulsing" zombies, distributed degradation-of-service is the moderated and periodical flooding of websites, done with the intent of slowing down rather than crashing a victim site. The effectiveness of this tactic springs from the fact that intense flooding can be quickly detected and remedied, but pulsing zombie attacks and the resulting slow-down in website access can go unnoticed for months and even years.[4]
Notable incidents of distributed denial- and degradation-of-service attacks in past include the attack upon the SPEWS service in 2003, and the one against Blue Frog service in 2006. In 2000, several prominent Web sites (Yahoo, eBay, etc.) were clogged to a standstill by a distributed denial of service attack mounted by a Canadian teenager. An attack on grc.com is discussed at length, and the perpetrator, a 13-year old probably from Kenosha, Wisconsin, was identified on the Gibson Research Web site. Steve Gibson disassembled a 'bot' which was a zombie used in the attack, and traced it to its distributor. In his account about his research, he describes the operation of a 'bot'-controlling IRC channel.[5]
Beginning in July 2009, similar botnet capabilities have also emerged for the growing smartphone market. Examples include the July 2009 in the wild release of the Sexy Space text message worm, the world's first botnet capable SMS worm, which targeted the Symbian operating system in Nokia smartphones. Later that month, Charlie Miller revealed a proof of concept text message worm for the iPhone at Black Hat. Also in July, United Arab Emirates consumers were targeted by the Etisalat BlackBerry spyware program. At the present time, the security community is divided as to the real world potential of mobile botnets. But in an August 2009 interview with The New York Times, cybersecurity consultant Michael Gregg summarized the issue this way: "We are about at the point with phones that we were with desktops in the ’80s.”
References
- ^ Tom Spring, Spam Slayer: Slaying Spam-Spewing Zombie PCs, PC World, 2005-06-20
- ^ White, Jay D. (2007). Managing Information in the Public Sector. M.E. Sharpe. pp. 221. ISBN 076561748X.
- ^ Weisman, Steve (2008). The Truth about Avoiding Scams. FT Press. pp. 201. ISBN 0132333856.
- ^ Schwabach, Aaron (2006). Internet and the Law. ABC-CLIO. pp. 325. ISBN 1851097317.
- ^ Steve Gibson, The Attacks on GRC.COM, Gibson Research Corporation, first: 2001-05-04, last: 2009-08-12
External links
- What is zombie and how to prevent from zombie
- Study by IronPort finds 80% of e-mail spam sent by Zombie PCs. June 28, 2006
- Botnet operation controlled 1.5 million PCs
- Is Your PC a Zombie? on About.com
- Intrusive analysis of a web-based proxy zombie network
- A detailed account of what a zombie machine looks like and what it takes to "fix" it
- Data and graphics related to zombie originated spam
- Correspondence between Steve Gibson and Wicked
- Zombie networks, comment spam, and referer [sic] spam
- The New York Times: Phone Hacking Threat is Low, But It Exists
- Hackers Target Cell Phones, WPLG-TV/ABC-10 Miami
- Researcher: BlackBerry Spyware Wasn’t Ready for Prime Time
- Forbes: How to Hijack Every iPhone in the World
- Hackers Plan to Clobber the Cloud, Spy on Blackberries
- SMobile Systems release solution for Etisalat BlackBerry spyware
Malware Infectious malware Concealment Malware for profit Privacy-invasive software · Adware · Spyware · Botnet · Keystroke logging · Web threats · Fraudulent dialer · Malbot · Scareware · Rogue security software · RansomwareBy operating system Protection Countermeasures Categories:- Computer network security
- Denial-of-service attacks
Wikimedia Foundation. 2010.